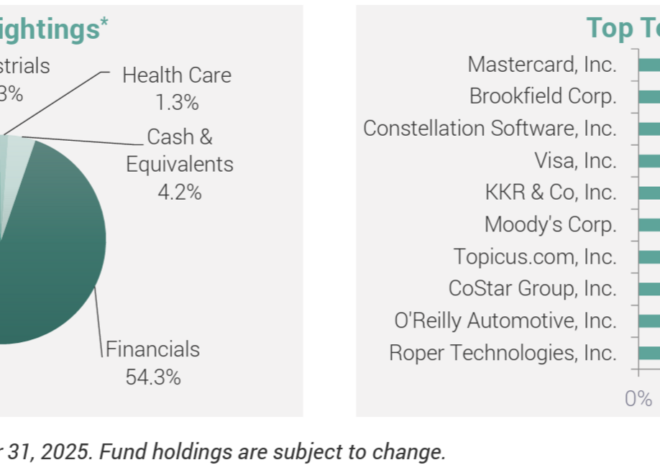
JP Morgan bets on Ethereum for its MONY fund
JP Morgan Chase & Co. has formally entered the contest for on-chain cash, and the prize is not just a new product line. It is the billions of dollars in institutional capital that now sit in zero-yield stablecoins and early tokenized funds. On Dec. 15, the $4 trillion banking giant launched the My OnChain Net […]