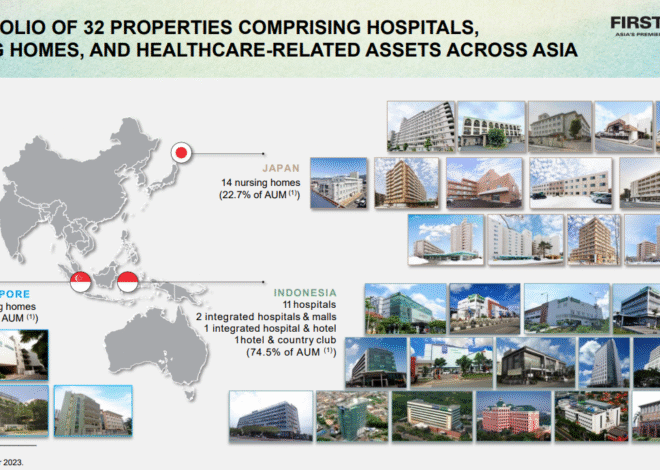
SEC approves new listing standards paving way for crypto ETFs on Nasdaq, Cboe, and NYSE
Key Takeaways The SEC has approved standardized listing rules for commodity-based trust shares. Nasdaq, Cboe, and NYSE can now list these products without individual SEC applications per product. Share this article The Securities and Exchange Commission approved generic listing standards for commodity-based trust shares on Nasdaq, Cboe and the New York Stock Exchange. The approval […]